I’ll know more when I can examine the data.

I ordered a ZModo home security camera kit that came with four cameras and a DVR box. After some time I noticed that the clock was drifting, then I remembered the ethernet port I’ve never used. You need to use Windows to even access the thing from a browser, so I never plugged it into the network.
Being the cautious and curious guy that I am, I preemptively setup a static IP address for it, added it to my ‘Botnet Of Things’ firewall group, activated tcpdump to watch the traffic, then plugged in the ethernet cable.
Right away there was a bit of traffic to sift through, but once the dust settled I saw something rather odd. It was sending HTTP request of GET / every 30 seconds. The server responded with 200OK. I pulled it up in a browser to see it for myself, and yup – successful page load, but a completely empty HTML document.
I did a whois lookup on the IP address, and it was located in China. This was enough for me. I unplugged the device immediately.
The very next day my network monitoring setup noticed a port scan coming from – guess where? China. After a few days of being offline, the device ceased to work completely. It had been running just fine for years, but okay.. fine by me. I bought a better DVR box that works with the same cameras.
In the meantime, however, I wanted to know more. I wanted to see the code. I started learning how I would go about that, and looks like I’ve finally gotten a good reason to learn hardware hacking! Sounds like fun. I learned about JTAG, SPI, UART, FTDI and such, then ordered some tools.
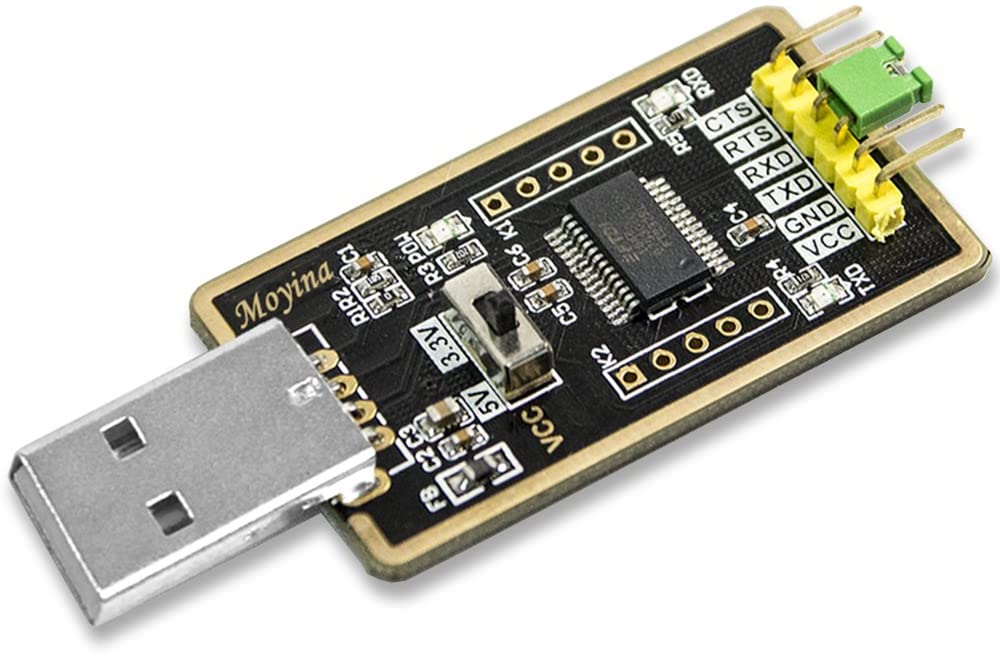
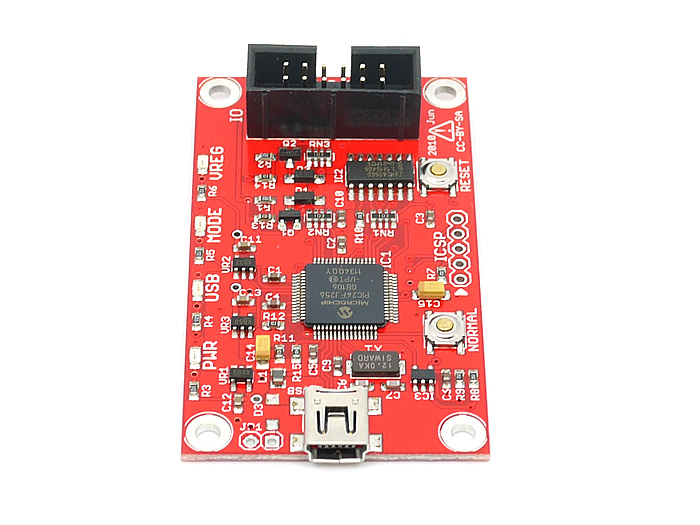
While I waited for these to arrive, I started examining the board itself to identify the purpose of each chip. In the end, I only found one that actually stores data. So there’s my target chip.
After finding the data sheet, I had a pinout:
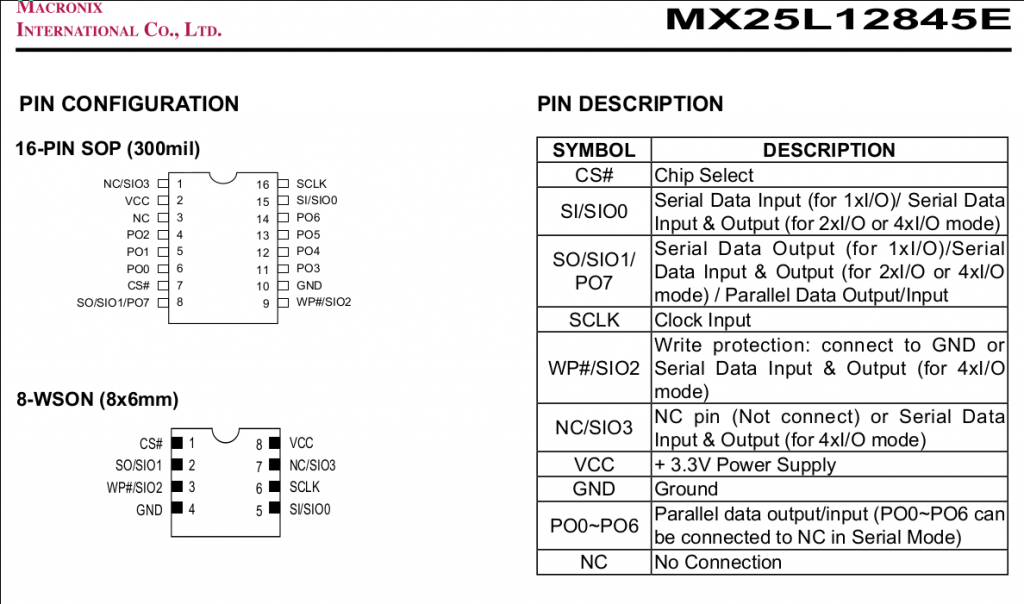
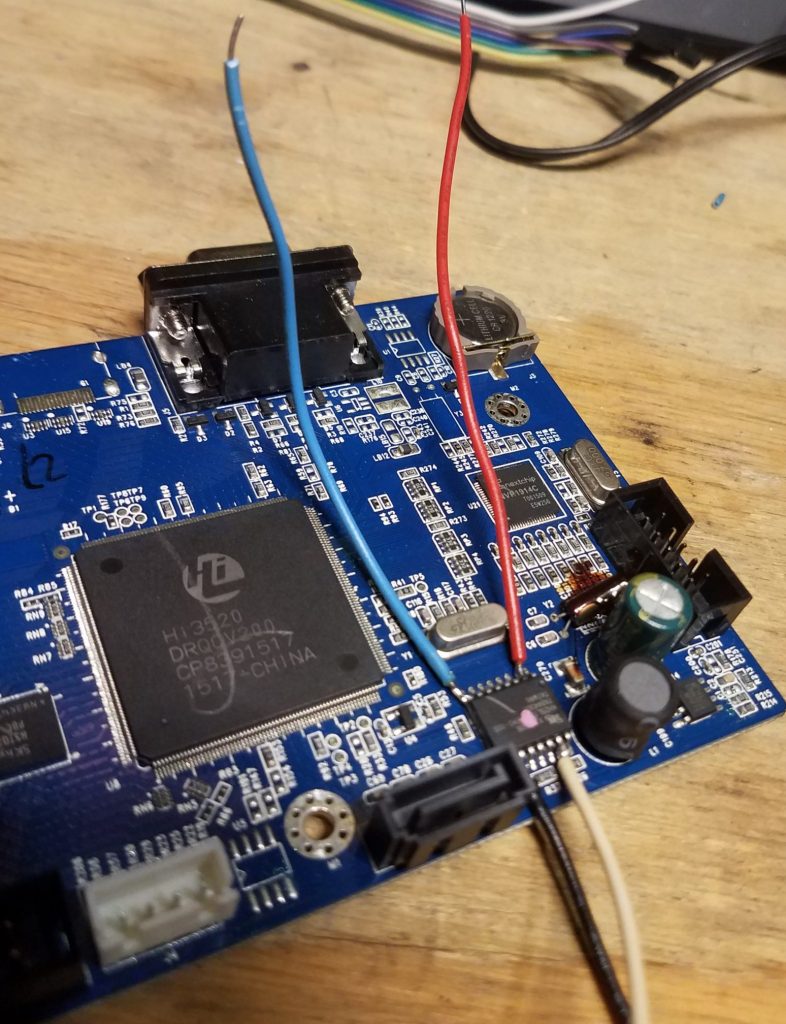
Unfortunately, this method fails as it usually does. The 3.3V being sent to it was leaking elsewhere on the board and causing interference. So I have to remove the chip completely.

Then I got it all wired up:
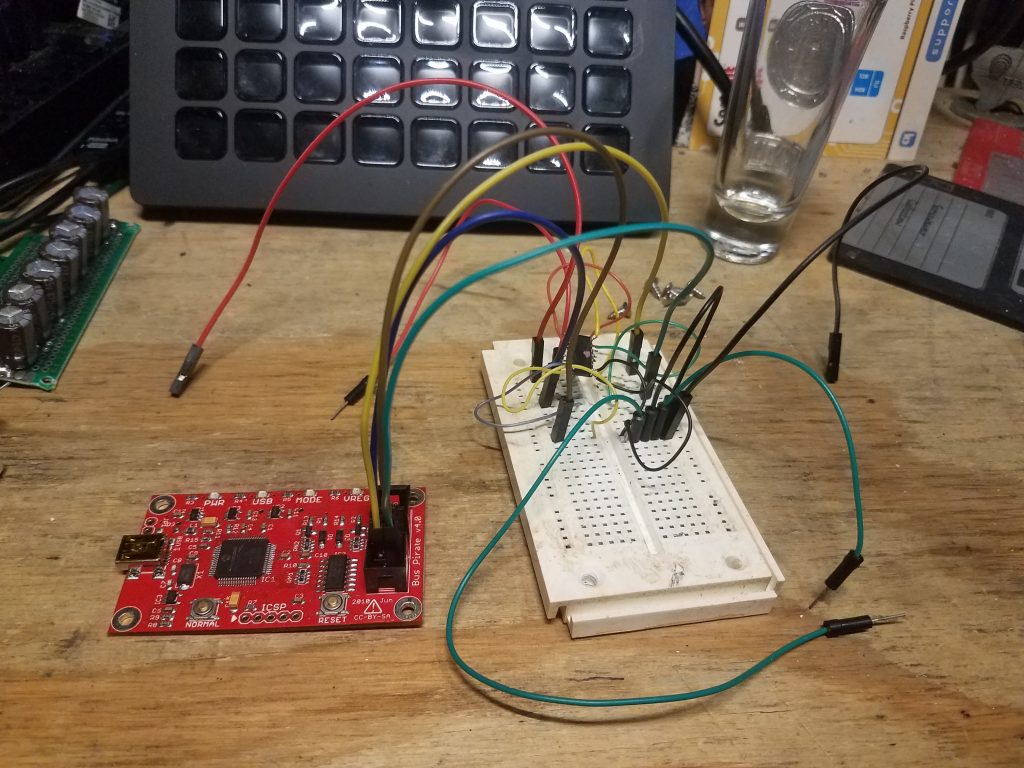
Unfortunately, this is where the story ends for now. I ran into a lot of problems with the firmware version the Bus Pirate shipped with, and getting it updated was a total PITA. Even after running a version that wasn’t failing to just maintain a USB connection, it didn’t seem to be able to pull data. Running the command to dump the contents simply…. stopped. Like it was waiting, but nothing was happening.
So I’m going to go back through everything to see what I missed, but I will point out that the chip does have a ‘full chip wipe’ command, and I wonder if that may be why the device just ‘failed’ suddenly.
